Teh Cookie Monster. A full example of how XSS can lead to full account takeover.

Security
Hacking My Bank. For teh lulz.
I lost count how many exploits I found in my bank. They have a huge attack surface.
Security
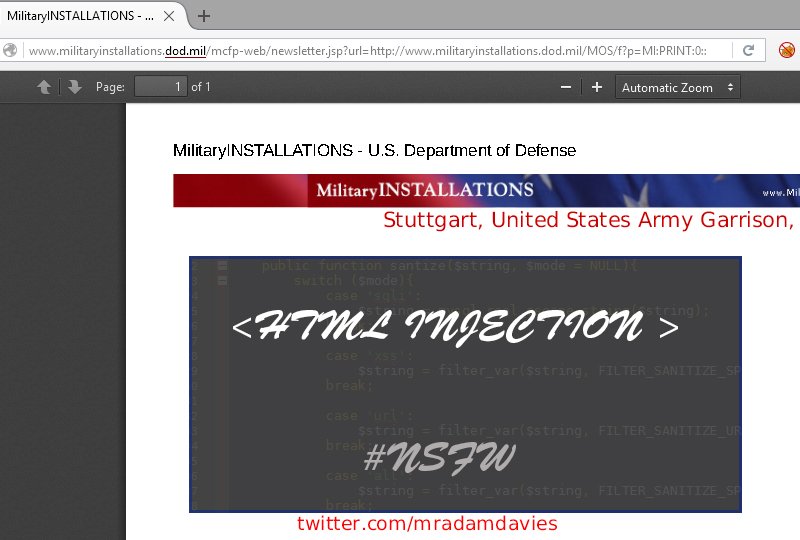
Mocking the Military; Hacking Hackers
I found a way to add pages to the U.S. Department of Defence. Of course I took the piss. Also, hacking hackers bonus content.

Security
Scoot.co.uk XSS
Stored XSS in several nationwide UK newspapers. One XSS to rule them all.

Security
How to: not get hacked
Most people don’t really care about security. We hope and believe our computers take care of security for us. Posting the latest Facebook update pretending to be our cat is…
Security
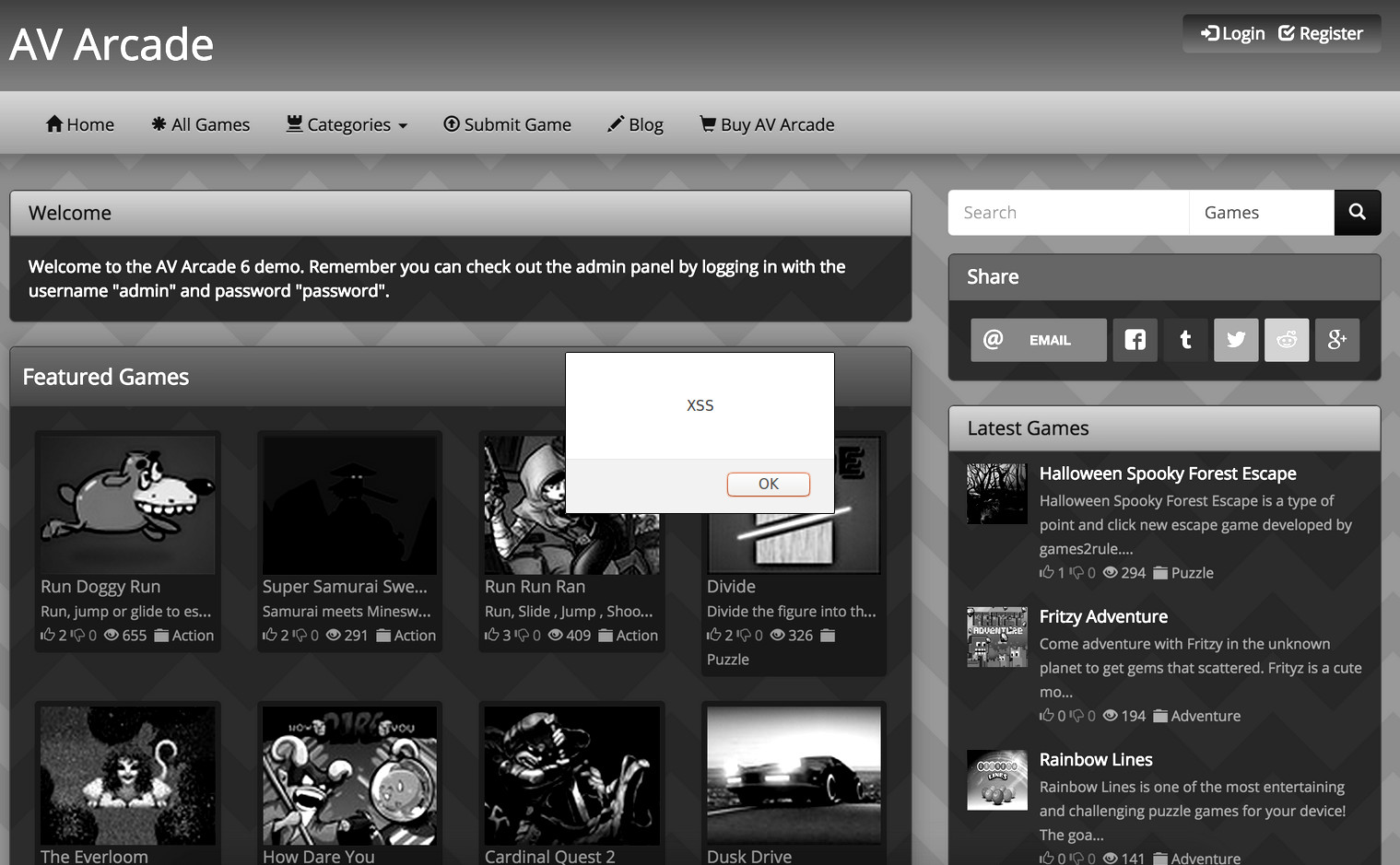
AV Arcade XSS Exploit
During registration, the user name field of the AV Arcade script is open to a stored XSS attack. Code will be processed on the members page. The malicious code can…