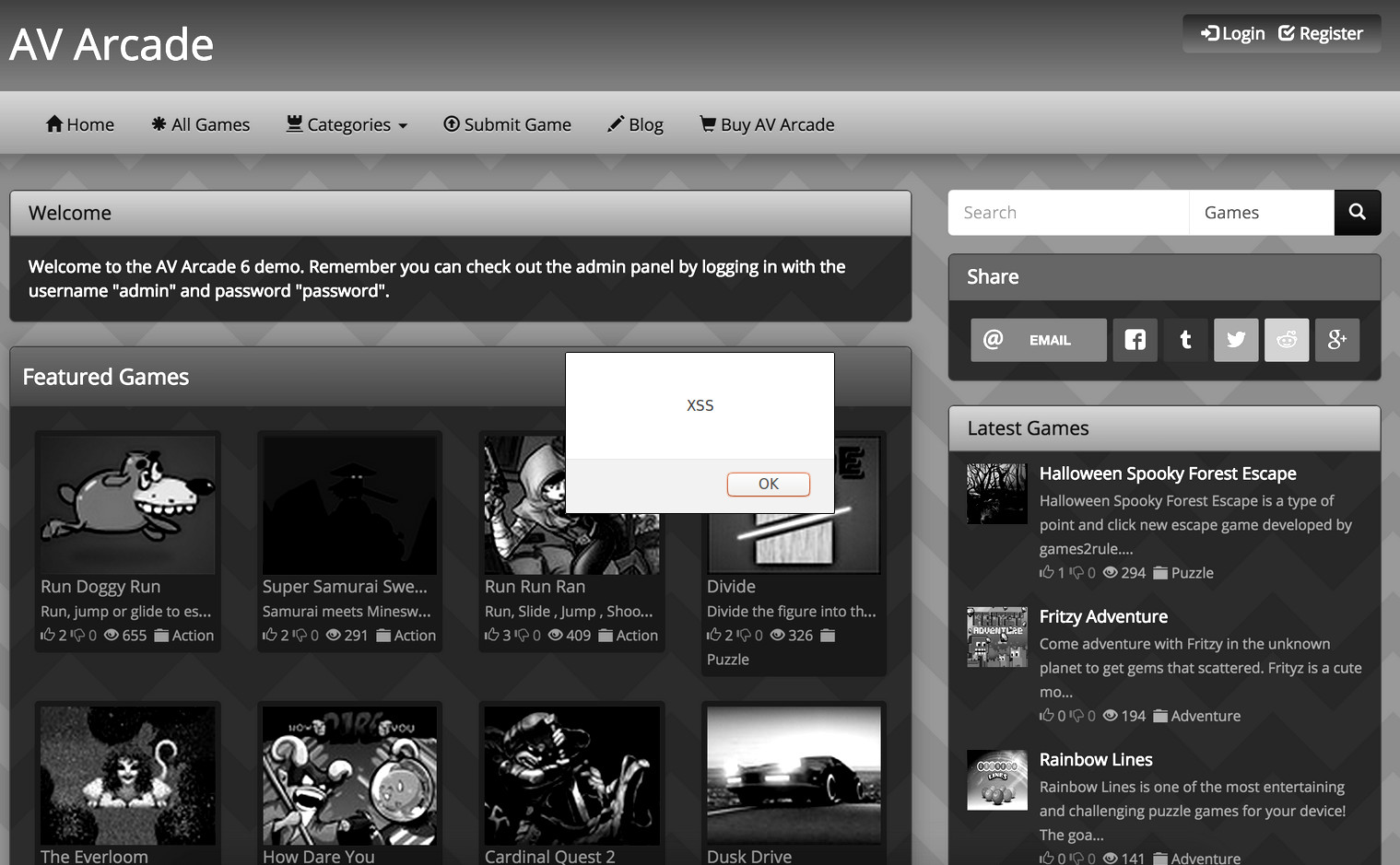
During registration, the user name field of the AV Arcade script is open to a stored XSS attack. Code will be processed on the members page.
The malicious code can be overflown to the homepage fairly easily. Almost XSS code can be used.
I would now consider this as a serious exploit and suggest fixing this bug A.S.A.P (Edit: This exploit was fixed. Keep AV Arcade up-to-date!)
The Fix
- Backup then open yoursite.com/register.php
- Find:
$info2 = htmlspecialchars($info); 1 $info2 = htmlspecialchars($info); - Add below:
$username = htmlspecialchars($username); 1 $username = htmlspecialchars($username); - Backup then open yoursite.com/admin/manage_users.php
- Find:
while($row = mysql_fetch_array($sql)){ 1 while($row = mysql_fetch_array($sql)){ - Add below:
$username = htmlspecialchars($username); 1 $username = htmlspecialchars($username); - Save and upload all files.
- Search your members list for any user names shown as code and delete (You could also I.P. ban them).
This function could easily be expanded for further validation. Thanks to dan20071 for letting me know about this!
Share Post:



Leave a Reply