Disclaimer: This post is probably not safe for work. Bad language, political views, and oxford commas aplenty.
This article covers a few basic cross site scripting bugs in Department of Defence and Ghost Security websites. The idea is to highlight how even the most security conscience among us can forget to check for the most basic exploits.
I love Einstein. I have always had a passion for physics, relativity, and politics. A little cited quote from the aforementioned scientific genius is…
Mocking the military
As much as I hate murder, the recent escalation of terrorism has been far worse. Another idol of mine – Bill Hicks – famously said: “I was in the unenviable position of being for the war, but against the troops. And ah… Not the most popular stance I’ve ever taken on an issue”.
War is bad, m’kay. Terrorism is worse, m’kaaay… Getting on with it.
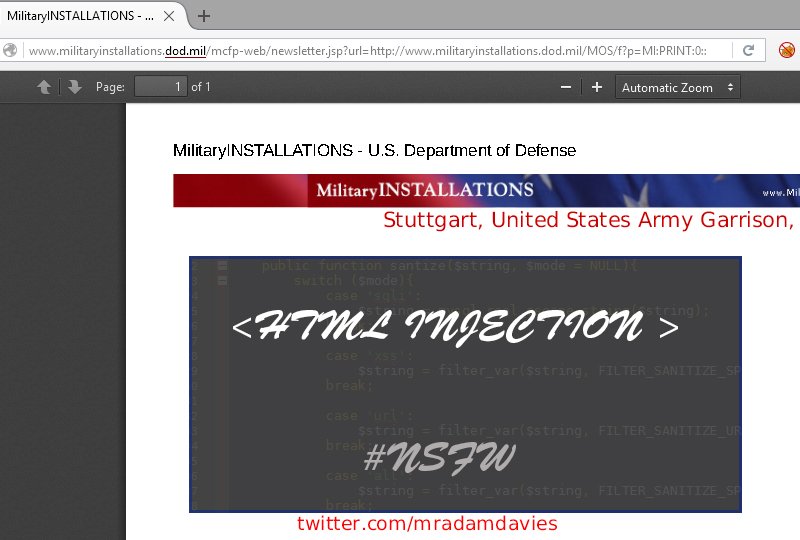
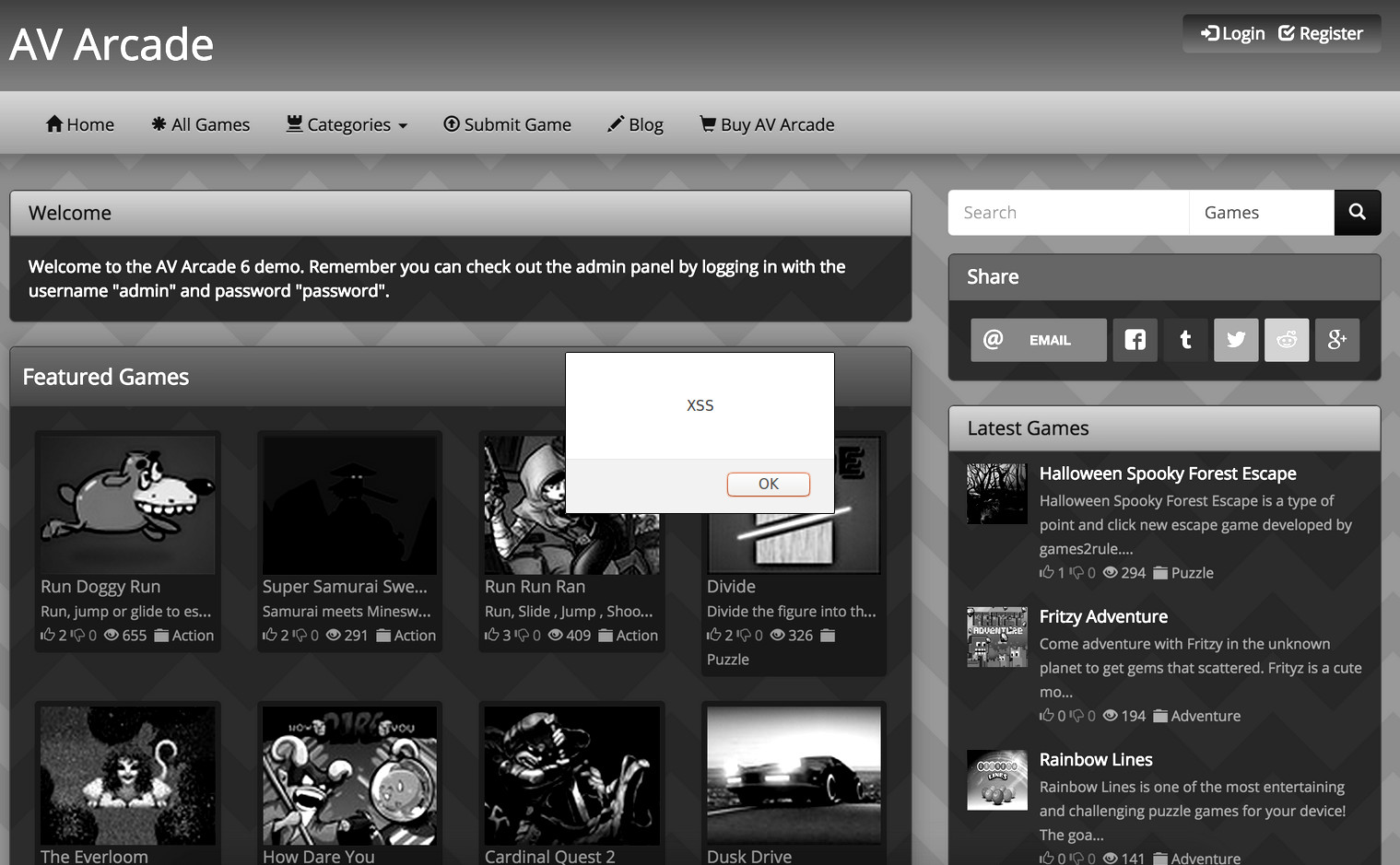
Cross site scripting is one of the easiest exploits to protect against, yet is one of the most prolific. The example below is a perfect example of an easily overlooked bug in a website that could cause a lot of damage. Simply altering a URL on the Department of Defence website allowed any HTML to get shown in the PDF document:
The vulnerable page was:
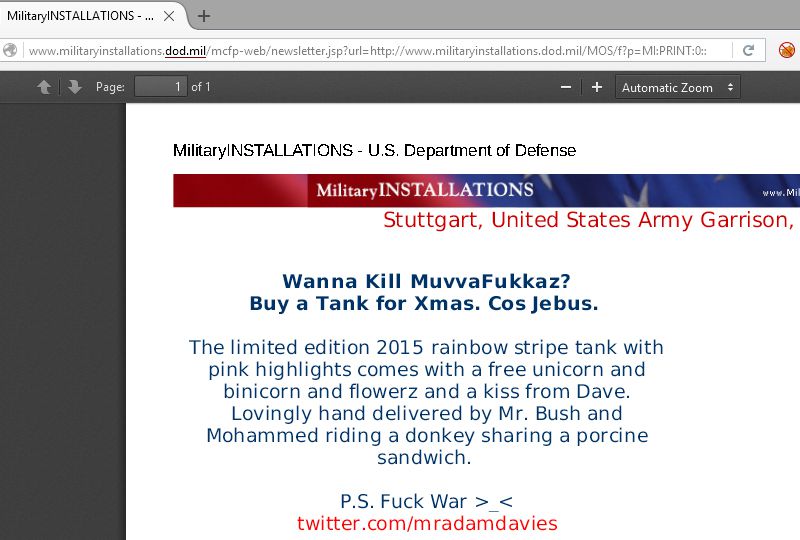
http://www.militaryinstallations.dod.mil/mcfp-web/newsletter.jsp?url=http://www.militaryinstallations.dod.mil/MOS/f?p=MI:PRINT:0::::P11_INST_ID,P11_CONTENT_TITLE,P11_CONTENT_EKMT_ID,P11_CONTENT_DIRECTORY:1930,[HTML_INJECTION] ....The Department of Defence responded quickly and a fix was rolled out within 24 hours. They confirmed the logic issue was fixed as there were several affected pages. I imagine the reply was sent through gritted teeth, but it got fixed and everyone is happy. Mostly.
I always email the site owner, wait 12 weeks, then try additional contact to get the issue resolved. Certain religious extremist groups may not be as helpful.
My sardonic proof of concept was intended to get a reaction. The vast majority of vulnerabilities go unfixed for months, even in government websites. I have reported hundreds of exploits on websites ranging from a plumber’s personal blog to wikileaks.
Hacking hackers
So we’ve mocked the military. Why not hack the hackers? I tried to use the same simple technique on a group I’ve morally supported for a while. Ghost Security are a splinter-group of Anonymous which specialise in combating the spread of religious extremism on the internet.
Surely, the uber-1337 hax0rz can protect against a simple XSS vector? Sadly not.
Even hackers make mistakes.
GhostSec are great guys and fighting for the right team by taking down extremists. I decided to check their website because T.V kills brain cells.
Within about 30 seconds I found a validation error in their hostchecker tool:
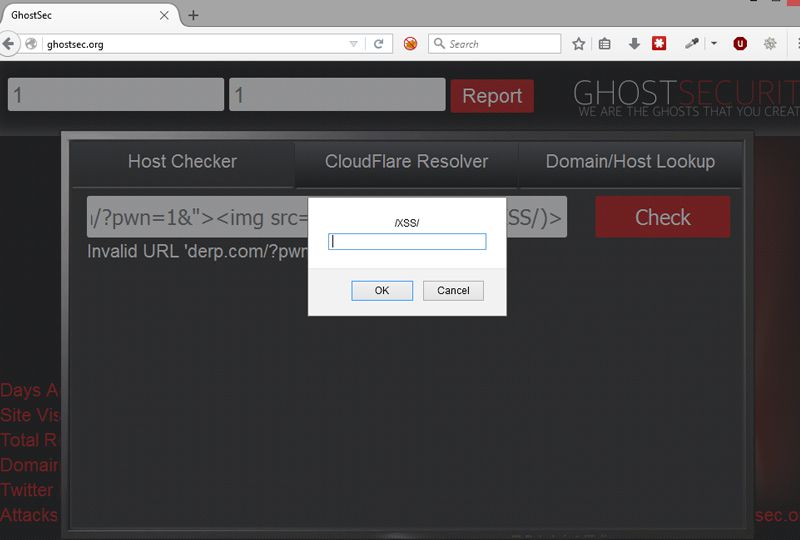
I notified them about this on Twitter. They added some basic input validation, replying with: “just feeding our XSS database ty”.
The proof of concept code used was, as always, basic:
derp.com/?pwn=1&"><img src=x onerror=prompt(/XSS/)>They eventually put some XSS security in place. I thought I’d test the hacker’s anti-hacker protection. Only a basic filter had been put in place:
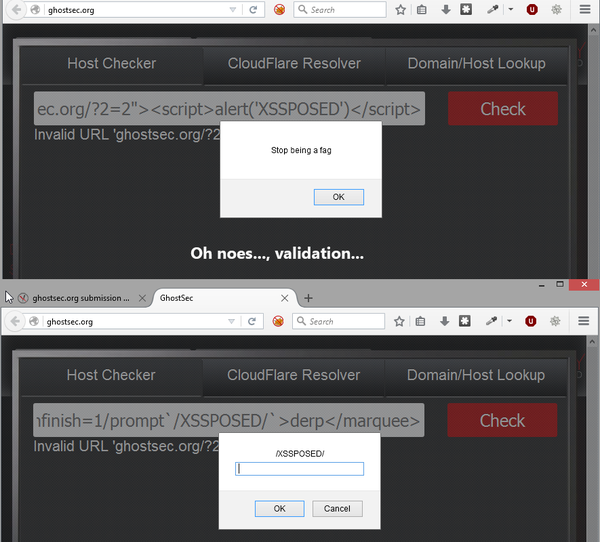
A common XSS WAF bypass technique worked. It took about 2 minutes:
derp.com/?pwn="><marquee loop=1 width=0 onfinish=1/prompt`/XSSPOSED/`>derp</marquee>The rest of the site seemed fairly secure so I moved on, after the obligatory bragging on social media. I read another story about them around 4 months later, so decided to check the once secure site. XSS number 3…
Trash or treasure?
The point of this rant is that even the the experts make simple mistakes. The only real difference is scale of impact. If I had been trying to recruit bad people to do silly things, it would be a very different conversation. From making websites dance, to hijacking accounts or stealing bank data…
If I can make your website dance, what are the bad guys doing? The code isn’t that different.
Update
I have been informed that Ghost Sec and Ghost Security are different entities. One apparently riding the fame of the other. The source is reliable and respected, so I trust it. The group split and skidz formed GhostSec. The story holds true as, initially, they didn’t seem to think XSS was an issue. According to press-releases, the original Ghost Security have beem known to use XSS and phishing techniques to hijack accounts. So, check out ghostsecuritygroup.com for comparison.
Feedback
The most frustrating thing is that cross site scripting attacks are the easiest to test for, most basic to protect against, indicative of weak security, and a risk on many levels. I’ve used similar techniques to circumvent world leading Web Application Firewalls, then helping to get patched, obviously.
I am genuinely curious as to why such basic exploits are still on such high priority websites. Could it be the budget is too small? Maybe the training isn’t good enough?
I’d really like to read comments from professionals and hackers alike, but hey, this is the internet – try to XSS my comment form if you must 😉


Leave a Reply